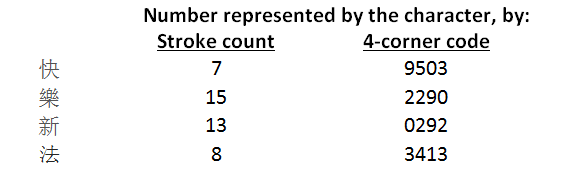Chinese characters may be used to code passwords in two ways that I know. One is stroke count and the other is the 4 digits from the 4-corner dictionary code. For example,
The 4-corner code has the advantage in that the 4 digits will come to mind quickly once you are familiar with the system. I would like to give more ideas on how we can use it for our purpose.
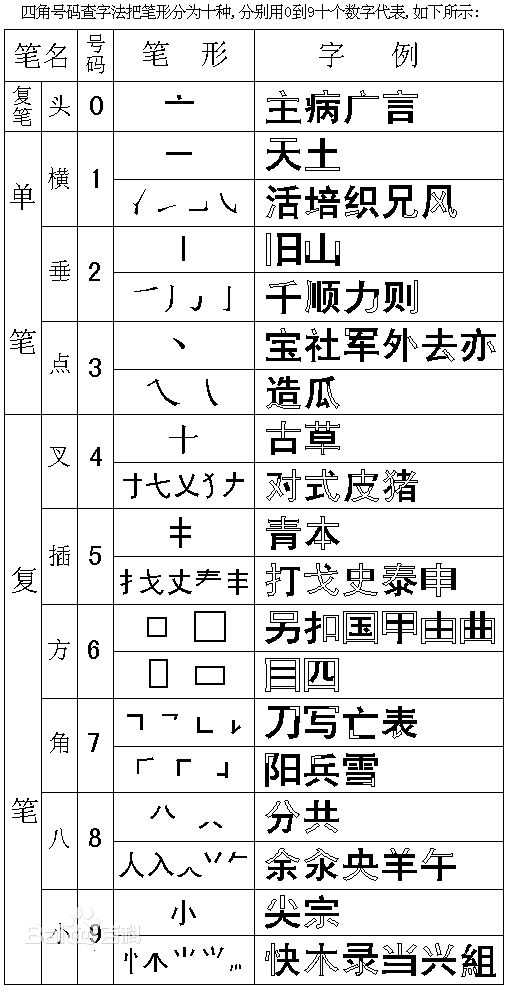
First, a reference chart on the 4-corner code or the 4-corner numbers character lookup system (四角號碼檢字法):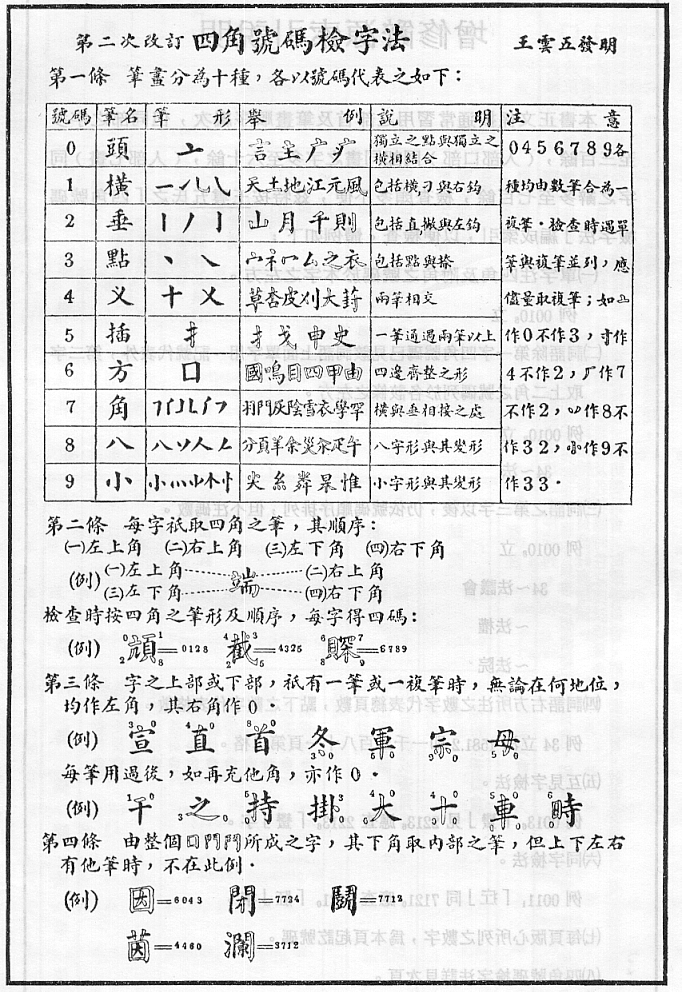
 Source: http://geostroke_abc.tripod.com/ChineseDigitalResearch.html
Source: http://geostroke_abc.tripod.com/ChineseDigitalResearch.html
This one for download into mobile phones for reference:
From: http://www.baike.com/wiki/%E5%9B%9B%E8%A7%92%E5%8F%B7%E7%A0%81
For those new to this system, there are many sites they can learn from. These are some of them:
http://dict.variants.moe.edu.tw/fulu/fu13/fubiau/four.htm
http://baike.so.com/doc/5430747-5669032.html
http://baike.baidu.com/view/67253.htm
http://www.chinaknowledge.de/Literature/Script/sijiao.html
This site gives the 4-digit numbers when you input the characters:
We can use Chinese characters to code either the constant or the variables. To ensure that there is a mix of alphanumeric characters, we should not have both the constant and the variables represented by Chinese characters. (There is of course no such constraint in the case of PINs.)
I would like to advocate the use of this strategy . Construct the constant to include the padding so that there will be letters in both upper- and lowercases, as well as symbols. Chinese characters are used for the variables. The list of variables will thus consist of Chinese characters. If we go one step further, if the Chinese characters are from the Chinese names of the websites or the organisations to which the websites belong, you can even dispense with keeping a list. For example: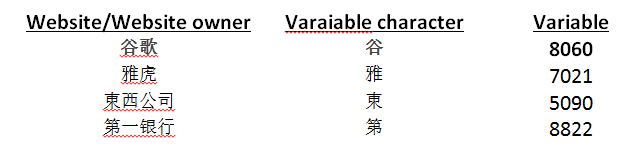
In the above examples, I use the first character of the name as my variable character. This is a rule I have set to apply in all cases. With this I can dispense with the need to keep a record of the variables. You can of course set a different rule, such as, taking the last character instead.
In conclusion, I would like to point out that this website will probably be known to hackers and cyber thieves. They will take note of this method. The primary strength of this method lies in the constant. We must make sure that it is never compromised and never something they can guess.
© Lim Jun Han