This posting is specifically for people who reside in Singapore. The NRIC, the organisations mentioned and the reference to the digitization practice now in use are in the Singapore context.
As a rule, we are not supposed to use personal numbers, like NRIC numbers, phone numbers, date of birth and address as passwords (PWs) and PINs. However, if we want to make use of things we will never forget, these numbers are among them. So, I’m going to show how we can use them without compromise to security.
The risk in using these numbers is that hackers will try with such numbers first when they want to break someone’s PW or PIN. Actually, what the rule is meant to bar is the use of these numbers in their exact form and sequence. If these numbers are used to construct new numbers in such a way that the original numbers are of no help, there will not be a loss of security. These personal numbers can be easily recalled as they are strongly etched in our memory. If we use one of them to work out a new number, we only need to remember the manner how it is manipulated. The reality is that it is easier to remember the manner of manipulation than to think of an entirely new number that has no association with something related to us. Numbers by themselves are difficult to remember because they have no images unless we can associate them with something known.
Here are examples how we can manipulate a number to construct new numbers from it. To make it easier to remember the process, I’ve coined terms for some possible manipulations, such as, “pow kow leow”, two-by-two, get even, hop step & jump.
For example, from a number, say 8214043, we can derive new numbers as follows:
1. “Pow kow leow”: 22 (Adding up all the digits)
2. Two by two: 70 (8+2 x 4+3) or 3526 (82 x 43)
3. Get even: 244 (Digits in even places)
4. Take on the odds: 8103 (Digits in odd places)
6. “You tou you wei” or pow tau pow buay”: 83 (First and last digits)
7. Backward rolls one two three: 340 (last 3 digits in reverse sequence)
8. Hop Step and Jump: 17 ( 8+2+4+3) or simply 8243
 For date of birth or any memorable date, write the date into a single number. E.g. for the date 16/07/82, write it as 16071982 and we can manipulate it in the same way.
For date of birth or any memorable date, write the date into a single number. E.g. for the date 16/07/82, write it as 16071982 and we can manipulate it in the same way.
Constant and Variables
The method of creating PWs and PINs is based on this formula:
PW/PIN = constant + variable
The constant consists of a number of characters that are applied to all PWs and PINs. The variable, as the name implies, varies for different PW/PIN. It can consist of characters that may be identified with the websites or organisations to which the PWs/PINs are meant for so that creating them will be easier. The total number of characters for a PW should be at least eight, but to be really strong it should be twelve or more. PINs are often limited to six digits. (See the posting on ‘Create Strong and Secure Passwords Easily’ for more information.)
The use of an unforgettable number to derive a new number for PWs and PINs is for the purpose of constructing a constant. We want the constant to be easily recalled so that there is no need to write it down.
Applications
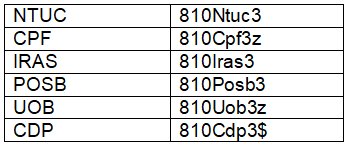
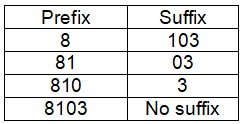
Applying the method in the Singapore context: let me use “8103” from example 4 above as my constant.
I will split it into 2 parts for a prefix and a suffix. It can be any one of these:
 This constant can be used for both PWs as well as PINs. For the variables, in the case of a PW, I use a word. For ease of memory, the words for the variables may actually be the names of the organisations they are meant for. For example, to access the NTUC Income portal, the word for the variable may be Ntuc. So, I’ll have my PWs for the various organisations, as follows, using option 3 to split the constant:
This constant can be used for both PWs as well as PINs. For the variables, in the case of a PW, I use a word. For ease of memory, the words for the variables may actually be the names of the organisations they are meant for. For example, to access the NTUC Income portal, the word for the variable may be Ntuc. So, I’ll have my PWs for the various organisations, as follows, using option 3 to split the constant:
- The name of the organisation should always have a mix of uppercase and lowercase letters. For simplicity, the above examples have the first letter in the uppercase.
- Make the PWs at least 8 characters in length. If the name is short, add a letter or number at the end. For the CPF and UOB examples, I add a ‘z’. In the case of CDP, I add ‘$’ because it requires a special character in the PW. Using the name of the organisation is a compromise but it is for the sake of ease of recall. However, considering that most organisations, especially banks, have a feature which will activate a lock-up after a certain number of failed login attempts, this compromise is quite acceptable.
- When I need to add a letter, number or special character, I will always use the same ones so that I’ll never forget.
- Do bear in mind that the method of manipulation you choose to work out your constant and how it’s applied in terms of splitting it into prefix and suffix, once decided, you must stick to this one particular method for all PWs. There must not be different manners of manipulation for different PWs. This is to make sure that there will be no problem with recalling the PWs.
- Actually, many organisations especially Government linked ones and banks now use the Singpass mobile app to perform verification for login without the need of a PW. This means having to login into Singpass with a passcode or by biometric means (facial recognition or fingerprint). Using a passcode means this has to be secure. Biometric means is more secure and convenient, although the passcode remains a backup in case the former fails.
PIN
I will discuss this section in the context of ATM cards because the PINs are usually limited to 6 digits. Four ways of deriving the variables are discussed here.
- Positions of the letters of the abbreviation of the organisations on the alphabet. For POSB, the number derived is 16151902. Since my constant has 4 digits (taking the same example as in the above 810_ _3), I require only 2 more digits. So I’ll take only the first 2 digits and my PIN will be 810163. If I had chosen a shorter constant, say ‘83’, then I’ll need 4 digits forthe variable which will then be 1615 and my PIN will be 816153.
- Numbers associated with the letters on the ATM number pad. POSB will give the number 7672. If I need only 2 digits for the variable then I’ll take 76

- Character counts of the words in the name of the organisations. POSB is Post Office Savings Bank giving the character counts of 4674.
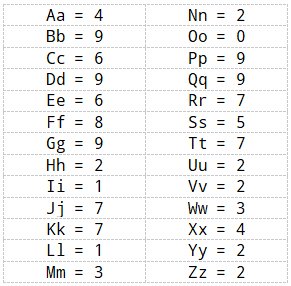
- Shapes of the letters An example of associating the shapes of alphabet letters with numbers
 A reference list for your handphone. Download here:
A reference list for your handphone. Download here:
Examples
Here is a chart showing how the different conversion methods will result in different PIN numbers, using the constant from “backward rolls one two three” with no prefix-suffix split
| Bank | Alphabet position | ATM/Phone pad | Character counts | Number shape |
| POSB | 3401615 | 340767 | 340467 | 340905 |
| DBS | 3400402 | 340327 | 340114 | 340115 |
| OCBC | 3401503 | 340622 | 340777 | 340069 |
| UOB | 3402115 | 340862 | 340684 | 340209 |
If the converted number has more characters than required, drop the superfluous ones (shown in red fonts above)
If there is no limit to the number of digits, then set your own so that you will have no uncertainty about how many digits for this and how many digits for that. Set a minimum of eight
Using Your Name
Another personal information that we cannot forget is our names. It’s of course a NO! NO! to use our names as they are. What we can do, if we are Chinese, is to use the Chinese characters of our names. The number of strokes that make up each character will give us three numbers if your name has three characters. If we ignore the surname then we have two numbers, one for use as the prefix and the other the suffix to form the constant.
For a name, let’s say, Lai Heng with these Chinese characters:
![]() The numbers of strokes are 7 and 16. Or, in simplified Chinese characters:
The numbers of strokes are 7 and 16. Or, in simplified Chinese characters:
So, there’s an option which means it adds another layer of uncertainty for hackers to figure out. Again, to emphasize, always stick to the option decided on. Strictly use only this one for all PWs and PINs to make sure there’s no confusion to cause problem with recall.
In fact, not only for constant, you may also use Chinese characters as a form of code for variables. Use meaningful and auspicious phrases so that it’s easy to remember. It will not be too much of a risk even if you write it down. To be realistic it is impossible not to keep a list of the variables if we want to have diffedrent PWs/PINs for different systems or organisations.
A Quick Action to Strength Your Present PWs
Before you start to reconstruct your PW/PINs to apply the system advocated here, you can take a quick action to strength your present PWs by adding a constant to them. At once, you’ll have added more characters to your PWs. This alone would have increased the number of permutations that will make hacking to break your PWs more difficult.
For example, take a PW that you have now, say, it consists of 5 alphabet characters, and you add a constant consisting of 4 numerical digits to it. A PW consisting of 5 characters is one out of 12.3 million permutations of 26 alphabet characters. If some of the 5 characters are in the uppercase, it’s one out of 387.6 million permutations of 52 lower- and uppercase characters. You can see how the chance of a strike is 300+ million more difficult. If we add 4 numerical digits to it, the strike chance is one in 1.04 x1014 (a 15 digit number). A tabulation comparing how much time required to break a PW of different lengths is shown here:

The calculations and estimates are made with the calculator in: https://www.grc.com/haystack.htm
You can see that increasing the number of characters to include upper and lowercase letters and numerical digits (even without special characters) would increase the strength of the PW many, many times. So, a simple way of increasing the strength of your present PWs is just to add a constant to all of them. Making the constant longer will ensure that your new passwords will have twelve or more characters. Work out a number from one of the examples above and add a memorable word to it and you’ll easily have six or seven characters for your constant.
As an example, let’s say I select 340 (“backward rolls one two three” from 8214043) as the number and I add “Warriors”, I’ll get “Warriors340” or “340Warriors” (the word must have upper- and lowercase letters to make sure that the eventual PWs will have both sets of letters) as my constant. This already gives me 11 characters and my actual PWs (constant + present PWs) will be pretty unbreakable. “Warriors340” is surely unforgettable and does not need to be written down.
Other examples for the constant are: Ofab340 (Old Friends are Best), Bto340 (Beating the odds), Wotm340 (Warriers on the move), Happy340, Peace340, Monkey340 (a Zodiac sign), Abc340 (initials of favourite relative’s name), etc.
PINs usually require a specific number of numerical digits. Hence it’s not possible to simply add more digits to them. It will be necessary to reconstruct them completely. PINs are mostly used in a Two-Factor Authentication (2FA) process. They are used in conjunction with another distinct device/system such as ATM cards, apps on a mobile or programs on a computer. A 6-number PIN can be broken in 19 mins in the case of an online attack and in less than a minute in offline brute-force attack. This means the need to keep the ATM cards safe and the mobile phone login authentication well protected although there are safety features that safeguard against unauthorised use. Remember ATM cards can be cloned and a mobile phone can be subjected to phishing and other cybersecurity attacks to steal personal/confidential information and credentials as well as allowing the attackers to take control of the phone (which enables them to intercept one-time passwords sent by the bank to authorise transactions). In the case of bank apps in mobiles, wherever possible use biometric means (fingerprints or facial recognition) for login and authentication purposes.
Lim Jun Han