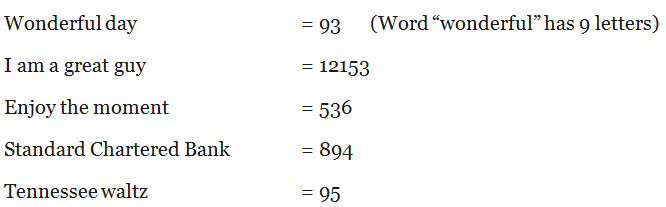Password = Constant + Variable
The Constant
The constant is the secret part of the PW. It is not written down anywhere. It is strictly in the memory. To make it easy to be remembered, we use a word that we will never forget because it has a special significance to us and nobody knows it. It may be a word that represents the moral principle we uphold, like honesty. Or, the name of a grandfather or grandmother or other favorite relative, a favorite flower, hero, pet, cartoon character, the first model of car we owned, zodiac/animal sign, a date, etc. Yes, it may be in the list of 500 worst passwords but the key to this method is how that word will appear in the PW. In fact, that word will not appear anywhere in the password. It will be split into two or more parts. In addition, the constant will include a padding for numeric characters and special characters (symbols) to be inserted into the PW. This is to ensure that the PW will contain characters from all four character sets and it is made up of at least 12 characters.
Again, in terms of a formula:
Constant = S~word + Padding
“S~word” represents a secret word.
The padding will consist of 3 or 4 characters other than alphabets. With some imagination, we can combined these characters to look quite meaningfully, viz: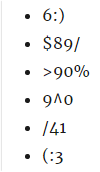
It will be inserted somewhere in the S~word. For example, “datsun” is a word that I will never forget because the first car I owned was a Datsun. I can use it as my S~word and I will insert the padding (5/>) into it, such as:
datsun + 5/> = datSU5/>N
“datSU5/>N” will be my constant which I commit to memory. Some of the letters are in the uppercase so that we have all four character sets in it. If this is what you have constructed, it will not be difficult to remember it. Datsun has the word “sun” in it, and I use the padding to break it up. I do not know if the word (i.e. any dictionary word in the PW) would be of any help to the hackers but I want to deny them any chance of getting a toe in. We must give due regard to their ingenuity to device the necessary tools for their purpose. So we have to anticipate the best we can.
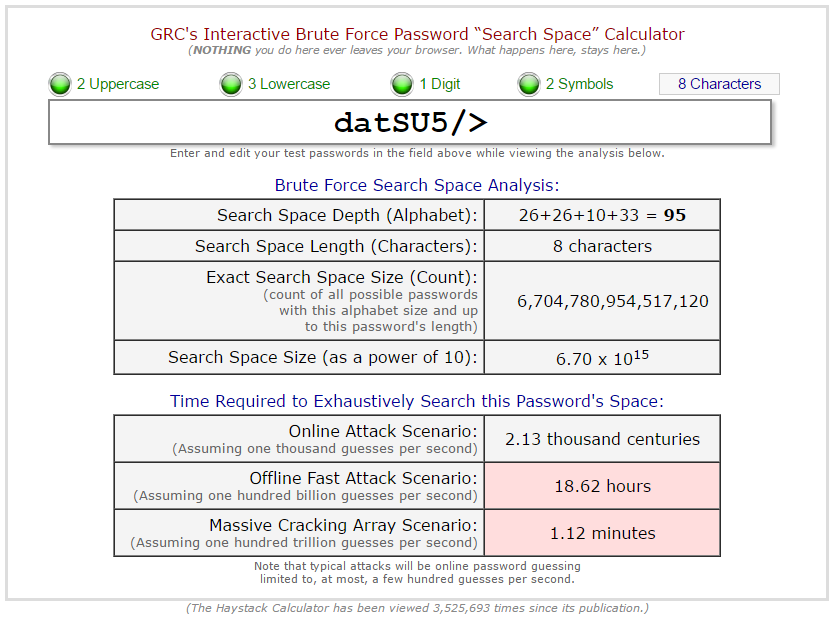
The padding serves another purpose: to ensure that the PW has at least 12 characters. The reason for this is to increase the odds against hackers making a hit. Gibson Research Corporation has a website where we can check on the length of time for a brute-force attack to crack a password. (https://www.grc.com/haystack.htm) For an 8-character password, it takes within a day to crack it, using offline fast attack.
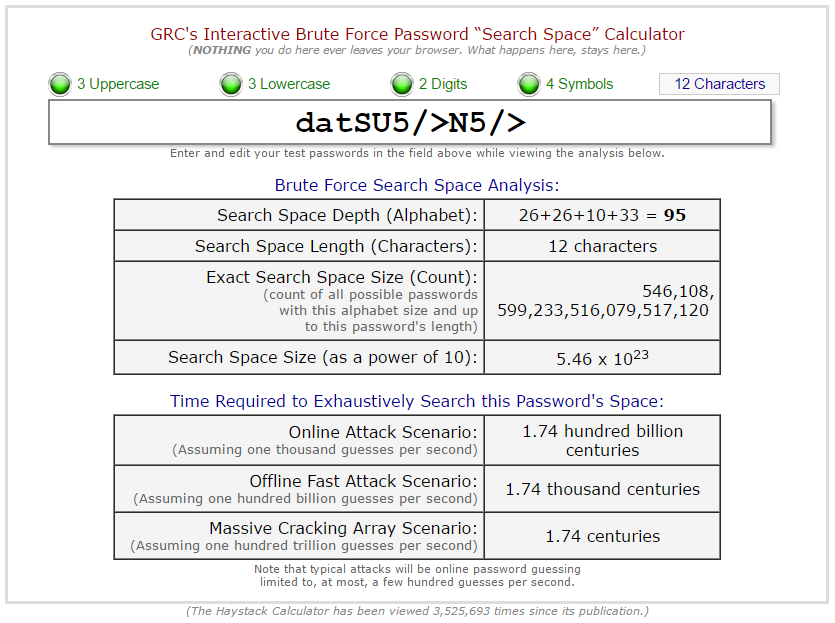
With 10 characters, it will take 19 years but when it is increased to 12 characters, it is almost impossible to crack. Even a massive cracking attack will take 1.74 centuries!
(See also http://www.infoworld.com/article/2655121/security/password-size-does-matter.html )
For websites or systems that do not permit the use of symbols in the PWs, then the padding will simply be the numerical digits in it. In the forgoing example, it is simply 5 and the constant is: “datSU5N”.
The Variable
The variable is different for different PW. It can be written down and if it is necessary to change the PW regularly, only this part is changed. Any word can be used as a variable but it will not appear in full in the PW. For example, if I have “beautiful” for the variable, the PW will be:
datSU5/>Nbtfl
All the vowels in the word “beautiful” are left out. You can see that the PW is hardly a recognizable word, but I am sure you will not have difficulty remembering it.
In this example, I have simply put the constant before the variable . You can actually set a different rule to how you apply the constant. You can have part of it in front as a prefix and the rest at the back as a suffix, such as:
datbtflSU5/>N
However, whatever rule you set, it must be that rule only in all cases. We must not give room for uncertainly as to how the constant is applied.
So what is written down for my PW is simply the word ‘beautiful’. My other passwords may be as follows, using the prefix-suffix rule for the application of the constant:
datrchdSU5/>N (variable = orchid)
dathppySU5/>N (variable = happy)
datrsSU5/>N5/> (variable = rose)
dattSU5/>N5/> (variable = tea)
In the last two examples, I have added another padding (5/>) to the back. Remember, one of the functions of the padding is to ensure that our PWs will have at least 12 characters. If they are shorter than 12-character length, we append another padding to the back. In general, all my PWs will take this form:
datvariableSU5/>N5/>
where the padding at the back (5/>) is optional, depending on whether there are already 12 or more characters without it. Although it adds to the complexity of the PWs, it will not take much of an effort to remember it. It is alright too if you want your PWs to always include a second padding so that you do not have to check whether you have more than 12 characters. For that matter, you can have a longer padding or a bigger word for the variable and dispense with the need of an optional padding. My purpose of pointing out more options is also to make the hacking job more difficult. We can expect hackers to read this website and would design their attacks to deal with this system. The more options the system can accommodate, the more secure this system will be. All you have to do for your purpose is to decide on one option, set your own rules and stick to them.
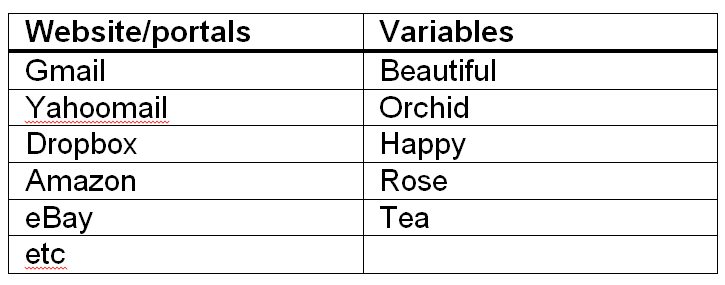
Going back to our examples, when we write down the variables, our list may look something like this:
You can see that the actual passwords are a far cry from the cues, i.e. the variables.
Numbers for Variables
An alternative to using words for the variables is to use numerical digits. This can be simply done by converting the words used for variables into numbers. There are several ways to convert words into numbers. I will show one way here. You can find more ways in the posting “Other Ways of Converting Words to Numbers”.
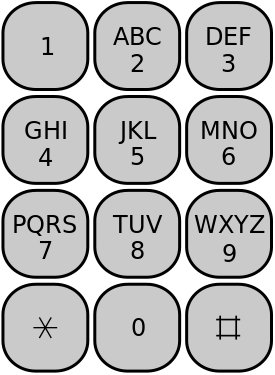
The telephone keypad has 3 or 4 alphabet letters associated to each of the digits 2 – 9. It provides a convenient way for converting words to numbers.
For our variables above they will be converted to:
So you can see that dat232884385SU/>N is not difficult to remember at all and neither is datbtflSU5/>N. For the former, the numerical digit in the padding is redundant and is left out. Again, it bears repeating that you have to decide on the rules for your system, whether you will have numbers for your variables.
For comparision, let me put the passwords side-by-side, before and after the variables are converted to numbers.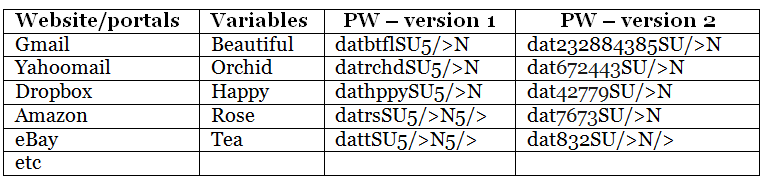
In version 1, the variables are the original words minus the vowels. In version 2, they are converted into numbers using the telephone keypad. This means that hackers will have to contend with an additional uncertainty even if they are able to get hold of the list of variables. There can be versions 3 and 4 if you can apply the other methods described in the posting “Other Ways of Converting Words to Numbers”.
Using a Phrase Another way of working out a number is to use a phrase. The number is obtained by the number counts of the words in the phrase. Example:
So the word phrases that provide the number codes are the variables. As can be seen above, we can use the names of public companies and song titles.
A phrase also offers another option for codding, using the first letters of the words:
Remember, the more options we have, the more secure our system.
Using Dates We can also use dates, especially for systems which require the passwords to be changed regularly. Use the date of the next change as the variable and you are also reminded of when you have to make the change. Example:
dat091817SU/>N or datspt1817SU/>N (spt for Sept)
If you do not want to write it down in your variable list, just make a note in your calendar on the particular date both as a cue and a reminder to change your password.
Conclusion
The whole system boils down to only the constant that needs to be remembered. In this regard, there are three considerations that you have to decide on:
If you use numbers for variables, then the padding does not need to contain numerical digits. Actually, there are other ways in which you can simplify your application of the system. I do not want to spell them out here for obvious reasons. You can customize it to suit your convenience as long as these basic rules are observed:
© Lim Jun Han