This website is for the purpose of sharing a system of creating passwords and PINs that are easily recalled yet not easily hacked. Unfortunately, it will also be read by hackers. A well thought out and well-protected constant is the best defence. There may be other strategies that can help make life more difficult for hackers. I would like to offer a few here.
First, let’s look at the listing of variables. Some may not be comfortable with the idea of putting the variables in a list. It may be seen as a give-away. But, think about it, it can also be used to mislead hackers. Here are some of the ways to do it:
Second, change the constant-variable-padding format. I can mix the components about as follows: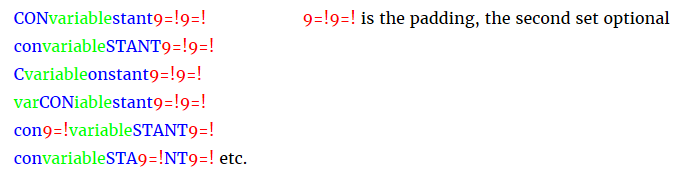
Third, use a big word for the variable but only the first, say 5 letters are applicable. For example, the word “celebration” will be become “clbrtn” without the vowels but we only use “clbrt” in the password. Or, if we drop all the vowels except “a”, then what is applied is “clbra“. Likewise, if we use numbers converted from words for variables, we can also apply a set number of digits only for the passwords.
The above examples are essentially to make the method more hack-proof even when the hackers know the method. I have given several examples how to go about encoding the constant and the variables. You only need to decide on one combination of two methods – one for the constant and one for the variables – and use just this one combination throughout. If necessary set your own rules, ones that work best for you. We want the system easy to use yet strong and secure. It will be so when we have no uncertainty in applying it and we are consistent.
I would like to invite contributions from readers if they have other strategies for encoding. The more varieties of ways there are, the more we are making the job of hacking difficult.
The more we share, the more we gain!
