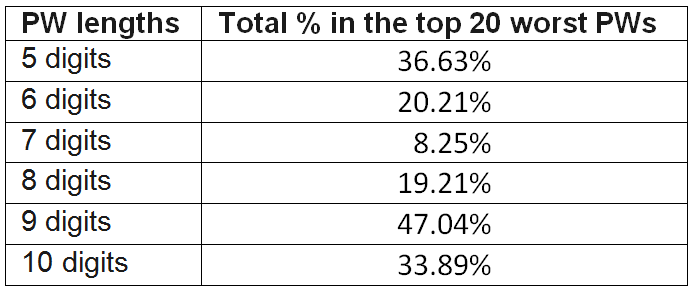
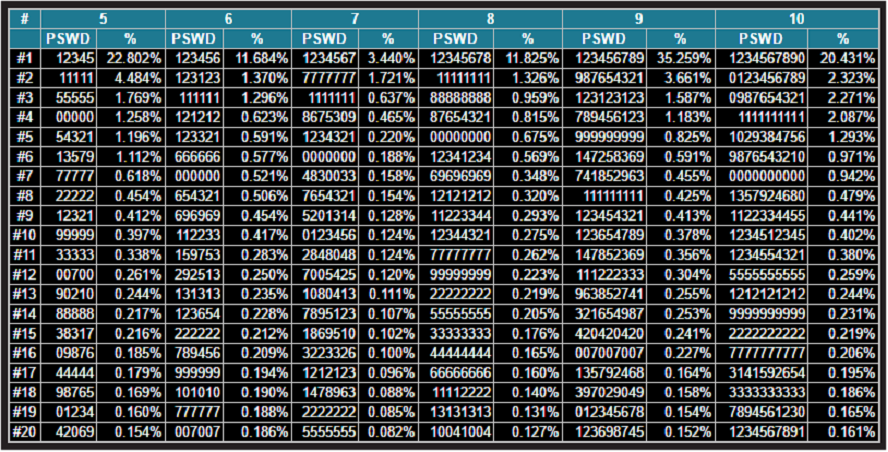
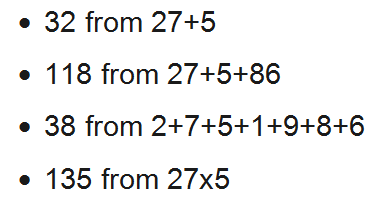We have seen the table produced by Data Scientist, Nick Berry showing the 20 most popular PINs of various lengths in the Introduction post. Here it is again:
 http://www.datagenetics.com/blog/september32012/
http://www.datagenetics.com/blog/september32012/
Nick points to another interesting observation. For 7-digit passwords, there is a significant drop in the number of people using the simplest of all, the 1234…. sequence. It is merely 3.4% while in all the other lengths of passwords they are more than 10%. There is also a significant drop in the total frequency registered by the usual types of top 20 worst passwords:
Nick speculated that a lot of people probably would at once think of their phone numbers when they were required to use a 7-digit password and therefore there were fewer occurrences of the typical worst passwords.
It can be said that it is a natural human instinct to fall back on what we already know when we have to work out something new. When it comes to numbers, what can be more handy than numbers closely associated with our identity and personal data. It is no wonder that there are so many people using such numbers for their passwords and PINs. Obviously, this is a poor way to protect our money if it has to do with drawing money from a bank account, which for most of us, this is what we need a PIN for. Hackers might be able to gain excess to our personal data and they will try their luck with them first. Or it might be a situation where our wallet is lost or picked and if our bank cards, credit cards, name cards and identity card are in it. We are putting more than just the money in the wallet at risk.
Since it is difficult for us to create something out of nowhere, we will develop a system that is safe for us to use these numbers.
We will apply the same basic principle as for passwords, only that we will work with just numerical digits. The components will again be constant and variable:
PIN = Constant + Variable
A difference here is that there is no requirement of a padding in the constant.
The Constant
The constant, just like for passwords, is the component that is not to be written down. As such, it must be one that is easy to create and then to remember. This is where we will make use of our personal numbers. We will use them as the starting points to transform them into new numbers. What we will do is to apply simple mathematical operations on them.
Take for example the date 27 May 1986, I can derive the number
Telephone numbers, national registration/identity numbers, social security numbers will become new numbers if we do one of these things:
So, you can see, there are as many ways of doing it as you can imagine and the numbers generated will have no resemblance to the original date or number. Since the number generated is meant for use as a constant, we will limit it to 2 or 3 digits. We want to leave room for the variables. Just a little imagination and the task is reduced to just remembering the particular personal number being used and what operation is performed on it. This is certainly much easier than trying to think of a random number and then remembering it. With so many ways to work out a number either from a date or other personal number, hackers will have a hard time even if they managed to gain excess to the personal data of their targets.
Another method Something else which we have a ready association with is the password constant. We can also use it for PIN by converting it into a number. In the posting on creating password, the telephone keypad is used to convert a word into a number for variables. We can do the same here. But it would be better to use a different method for constant. Since we only need to do it once, a slightly more involved method is preferable. Actually it is not a difficult method, only that it is not as straight forward as using the telephone keypad. Here, we assign a number to each letter of the alphabet based on its position in the alphabet: a = 1, b= 2, c = 3, ….. x = 24, y = 25, z = 26.
A number can then be derived from a word by adding the numbers represented by the letters that make up the word. For example, the word ‘datsun’ will be the sum 4+1+20+19+21+13 giving the number ‘78’. This way the word ‘datsun’ is my constant for both passwords and PINs.
The Variable
For the variable, we just have to come up with a word that can be converted into a number with the necessary number of digits to add to the constant to satisfy the requirement. We use a word rather than a number because words are easier to recall. They have meanings which can help us create visual images that provide clues to their recall. Moreover, if you have to write the word down, it will not be much of a giveaway because it will give different numbers depending on the method of conversion, as we will see.
So, if we need a 6-digit PIN, and our constant has 2 digits, we will need a 4-letter word to give us 4 digits to add to it. One that comes to mind is the word “flag” and I visualize the bank card fluttering like a flag on top of a flag mast, a mnemonic technique. I am sure you can create images associated with either the bank card or the ATM or both with words like, gold, hand, draw, shop, ship and sail. If I use “flag” as my variable, and “datsun” is my constant, my PIN will be one of these, using the telephone keypad to convert the variable:
I do not have to stick to the prefix-suffix rule here and I can insert the constant anywhere. This is to increase the possible combinations and thereby the odds against its being compromised. Of course, I will have to remember where the digits are inserted and apply them the same way in all cases.
The telephone keypad method is perhaps the easiest way t o apply. With the word in mind and the telephone keypad on the handphone by the side, it will be very easy to key in the PIN number. Some ATMs even have their number pads showing the letter associations.
o apply. With the word in mind and the telephone keypad on the handphone by the side, it will be very easy to key in the PIN number. Some ATMs even have their number pads showing the letter associations.
To increase the odd further, I can use a longer word for the variable and then ignore the vowels. I can also use a different conversion method to produce a different number. For example, the word “spark” can give different numbers as follows:
 See posting on “Other Ways of Converting Words to Numbers” to see how I get the numbers for examples c and d.
See posting on “Other Ways of Converting Words to Numbers” to see how I get the numbers for examples c and d.
Finally, you can also apply the method of using phrases for the variables as described in the post “Create Strong and Secure Passwords Easily”.
© Lim Jun Han